Blog
What is Network Monitoring
Network monitoring involves the continuous surveillance of a computer network to detect issues such as slow traffic or hardware failures. Specialized tools are utilized to scan the network and alert network administrators through various means, such as text messages, emails, or communication platforms like Slack when problems arise. Unlike network ...
The Art of Proactive Network Monitoring
Imagine being in a chess match where you can foresee five moves ahead, planning your strategy accordingly. That's the essence of proactive network monitoring. Rather than waiting for and reacting to problems, this approach allows you to anticipate issues and maintain a smoothly running network. This article explores the concept ...
Top 2024 IT MSP: CRN Recognizes a COUPLE of GURUS
a COUPLE of GURUS announced today that CRN®, a brand of The Channel Company, has named to its Managed Service Provider (MSP) 500 list in the Pioneer 250 category for 2024. The MSP 500 list compiled by CRN serves as a comprehensive guide to identifying and recognizing the top Managed ...
Why Regular Network Health Checks Are Business Critical
The health of networks plays a pivotal role in ensuring seamless operations across various industries. From facilitating communication to managing critical data, networks are the backbone of modern businesses. Understanding why regular network health checks are business critical becomes imperative to sustain efficiency and productivity. Importance of Network Health Checks ...
How to Ensure Your Cyber Insurance Pays Out in Manufacturing
The importance of cybersecurity and, by extension, cyber insurance cannot be overstated, as the manufacturing industry increasingly relies on technology. Cyber threats pose significant risks to manufacturers, making it crucial for businesses to invest in cyber insurance and ensure that it pays out when needed. This article explores the key ...
What is Cyber Liability Insurance in Manufacturing
Today, where manufacturing rely heavily on technology, cyber attack threats loom. Cyber Liability Insurance, often called Cyber Insurance, has emerged as a crucial risk management tool for manufacturing. This article explores the nuances of Cyber Liability Insurance, covering everything from its definition to potential scenarios and future trends. What is ...
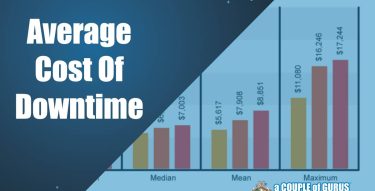
Average Cost of Downtime in Manufacturing
In manufacturing, "time is money" holds true. The sector revolves around the imperative of efficiency, wherein even a brief interruption in production can result in notable financial consequences. This leads us to the crucial notion of 'downtime'—a period of idleness or non-production universally feared by manufacturers. However, determining the monetary ...
New CMMC Proposed Rule
The Department of Defense (DoD) disclosed its long-awaited proposed rule for the Cybersecurity Maturity Model Certification Program (CMMC) on December 26, 2023. This regulatory framework, focused on cybersecurity, is poised to have a considerable impact on the majority of government contractors. The rule applies to contractors engaged in the processing ...
Why Is My iCloud Not Backing Up?
If you've ever found yourself frustrated because your iCloud isn't backing up as it should, you're not alone. Many users encounter this issue, and understanding its reasons can help you troubleshoot and resolve it. In this blog post, we'll explore the common reasons why your iCloud might not be backing ...