The importance of a conditional access policy
The cloud has revolutionized the productivity of many firms. Stakeholders are able to easily access files, applications, and systems remotely, increasing their efficiency and flexibility. However, these benefits come with additional responsibilities. Unregulated accessibility provides an easy opening for hacking and theft. Therefore, additional security precautions are needed to prevent unauthorized access.
Microsoft Business 365 addresses these concerns with its Conditional Access, a security feature that benefits businesses that utilize the cloud and need to grant their employees remote access. And for those in Minneapolis-St. Paul, A Couple of Gurus can guide them through the process of creating their own conditional access policies and expediting their launch, so they can begin protecting their assets as soon as possible.
What is conditional access?
Conditional access adds a layer of security to an organization’s network by enabling an administrator to regulate remote connections via policies, or “conditions.” These conditions go beyond the standard ID-based authentication to regulate the user’s location, the device being used, and the application or file being accessed, among other things. Failure to meet these conditions can lead to access being denied, or additional login credentials being required. This can take the form of an additional password, verification via mobile device, or other such second-factor methods.
What do you get from it?
Conditional access blocks unauthorized users from accessing sensitive or private digital assets, thus reducing the possibility of security incidents. In addition, conditional access prevents authorized users from sharing or creating copies of proprietary information. In most cases, conditional access meets and often exceeds the security requirements of HIPAA.
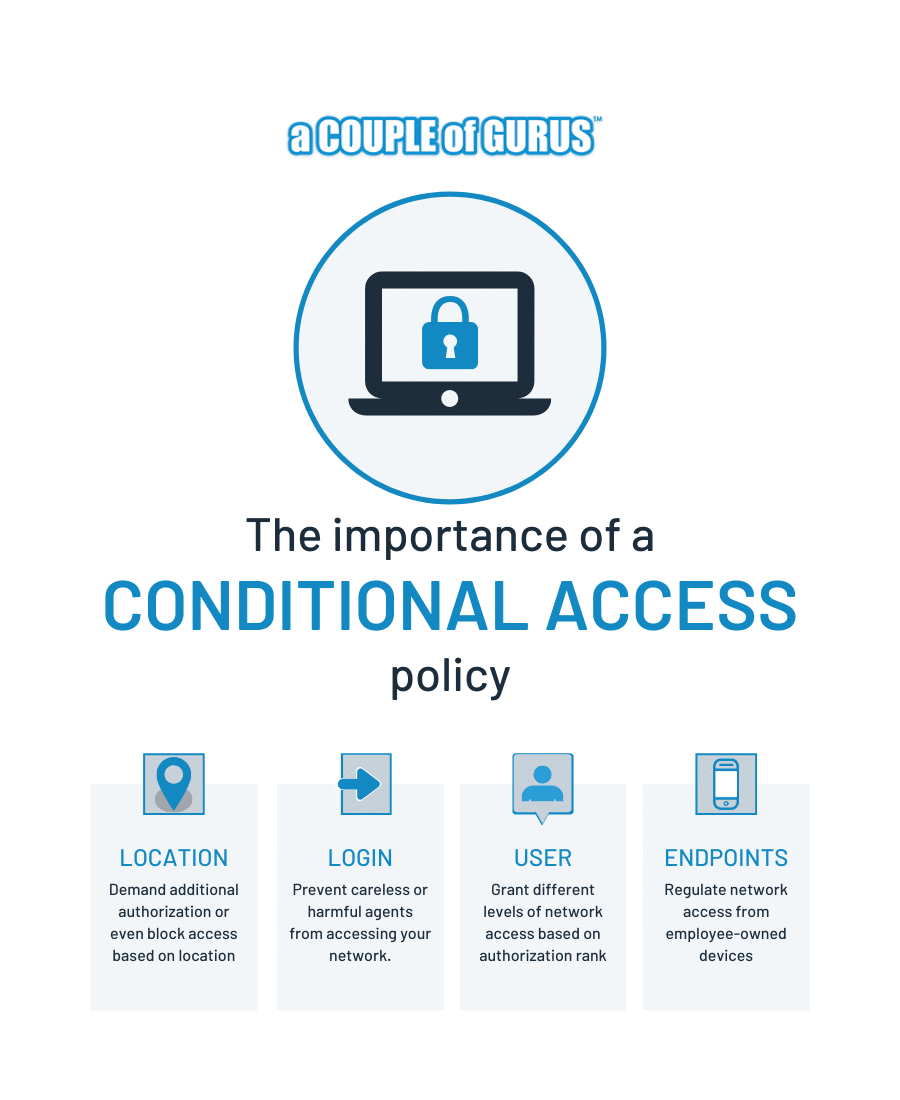
How does it work?
Conditional access can function on the following bases:
- Login
The technology detects whether access requests are secure or not, and it assesses the security risks of such requests. This prevents careless or harmful agents from accessing your network.
- Location
Administrators can demand additional authorization or even block access based on where the access request is geographically coming from. Conditions can be set to authorize requests from specific locations, like branch offices, or to require additional security for any locations outside your IT department’s control, for example outside a 100-mile radius from headquarters.
- Users
Individual users or groups of users can be granted different levels of network access based on their needs or authorization rank. Only those users whose work requires the use of sensitive files or resources are allowed remote access to them. Users with lower authorization levels will be denied, or will need to provide additional authentication for access.
- Endpoints
Access from employee-owned devices, such as personal laptops and smartphones, can be regulated. This includes limiting the number of employee-owned endpoints allowed to access your company’s network. Access can also be limited to particular devices within the control of your IT department.
For a real-world example of conditional access in action, let’s consider a company that bars access to sensitive information from high-risk devices and networks. If a user attempts to log in on a device with outdated software while connected to an unsecure public WiFi network, their access will be blocked. Conditional access automatically evaluates the safety of the device and network, making sure they’re patched and protected from attacks. It then offers instructions to remedy the issues, which ultimately minimizes the risk of a data breach and reduces the need to call help desks.
Now that more businesses are mobilizing their workforce and working outside the corporate perimeter, conditional access solutions are more important than ever. They provide a systematic way to secure your digital assets and ensure users have streamlined access to the resources they need to do their job.
A Couple of Gurus is an Office 365 security specialist. We will help you set up your conditional access policies, ensuring they are tailored to your company’s particular needs. Call us now, and we’ll get you started right away.




